Malicious attacks by hackers and state-sponsored actors to disrupt industrial control systems using SCADA is a growing concern. Recent breaches of SCADA network security in Ukraine, the United States and other nations have underscored the seriousness of the threat.
As a result, the U.S. government has issued an advisory warning that hackers have made attempts to “gain full system access to multiple industrial control system (ICS)/supervisory control and data acquisition (SCADA) devices.” These attempts have targeted certain programmable logic controllers (PLCs) and OPC UA servers.
Supervisory Control and Data Acquisition (SCADA) networks are at the core of every nation’s critical infrastructure. Therefore, malware and other cyberattacks are frequently targeting SCADA systems for public services. Some of the most vulnerable targets include power distribution, water treatment, oil and gas, and transit systems. It is essential that managers of SCADA systems ensure access and control of systems are protected from security breaches.
“Real security is building a moat around the SCADA castle,” says Mike Kirk, Director of Software Engineering for Nucleus Command Systems. “Keep it simple. Use air gaps between the local networks that do process control, and the open networks that provide information to management and interested outside observers.”
Here are some steps that the FBI and other cybersecurity experts have recommended that SCADA network security professionals can take to combat cyberattacks:
- Isolate ICS/SCADA systems and networks from external networks and make efforts to strictly limit any communications entering or leaving SCADA operations.
- Upgrade your SCADA software platform to modern products with secure and redundant network architectures.
- Regularly change passwords, utilizing device-strong pass codes that make it difficult for malware.
- Use multifactor authentication for any and all remote access to networks and devices.
- Limit access to SCADA network connections to necessary workstations and control and monitor licenses.
- Implement robust log collection and retention from SCADA systems and subnets.
- Consider employing continuous OT monitoring and use CISA’s open-source Industrial Control Systems Network Protocol Parsers (ICSNPP).
- Only use admin accounts when absolutely necessary, for tasks such as installing software updates.
- Ensure that USB ports are isolated and that laptops, phones and tablets connected to SCADA systems have robust anti-virus software installed.

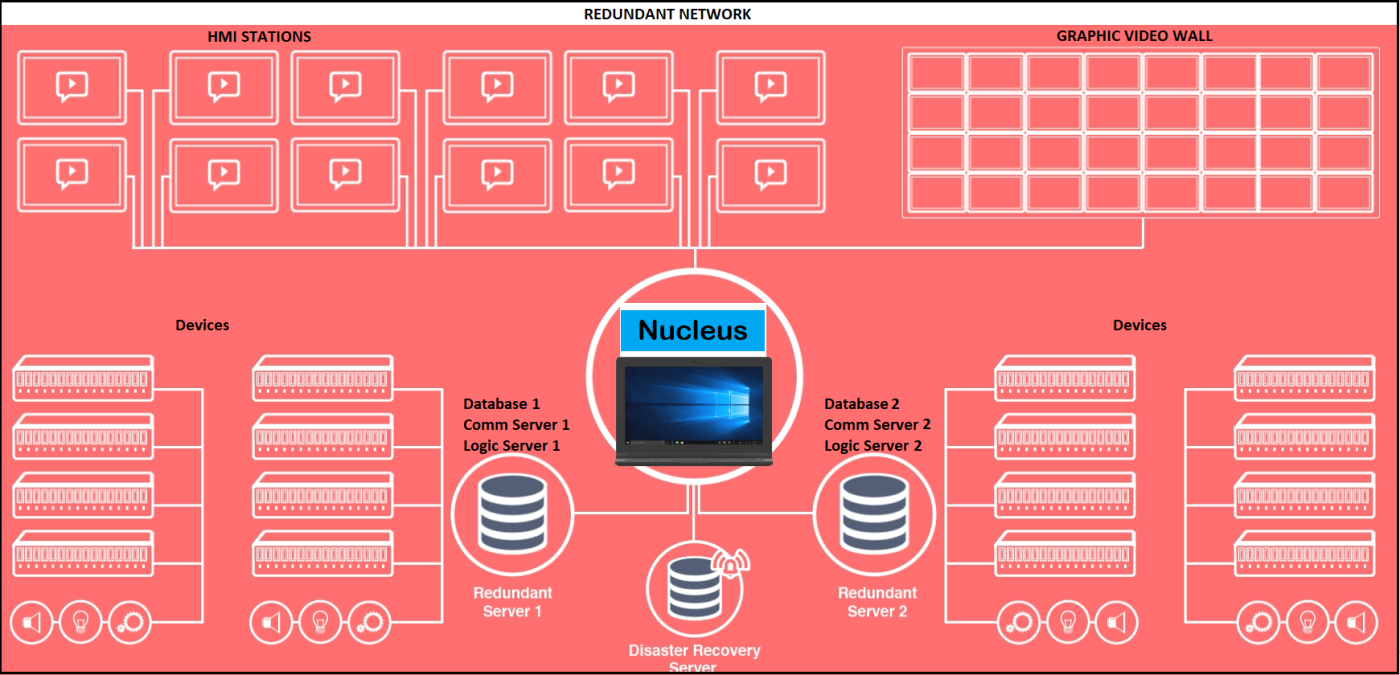
The most potent way to protect your SCADA system is by upgrading your entire SCADA software system. Modern SCADA platforms, such as Nucleus. “The Nucleus platform safely and securely operates in major urban transit systems, as well as other industrial applications,” explains Ken Baker, Sr. Director of Business Solutions for California-based Nucleus Command Systems. New systems can offer protection that older systems cannot. So when considering an upgrade of your SCADA package, experts recommend that cybersecurity be among the highest priorities.
Any good defensive strategy to protect your data is to start with realizing cyberattacks focus on weaknesses in SCADA systems. But if there are holes in your ICS or SCADA system’s defenses, perpetrators will seek to exploit them. The costs to such breaches can be extremely high, making efforts to continually secure your network a high priority.
But by taking SCADA network security precautions to protect your system, any damage can be eliminated or mitigated.
For a free consultation on SCADA system upgrades and security precautions, contact our Nucleus team at info@nucleuscommand.com.

