When it comes to selecting a SCADA software platform to monitor and control your industrial process system, price often becomes paramount. But how can you avoid going over your budget? Here are four key questions to ask to help you control the overall cost of your new Supervisory Control and Data Acquisition (SCADA) software system […]
Unless you’ve been on an extended vacation to Mars without any contact with Earthlings, you’re probably aware that there has been a lot of buzz about electrical vehicle manufacturer Tesla being a major disrupter in the automotive world. The disruption is broad and real: A unique retail sales model. Advanced battery technology. Its entire industrial […]
A quick web search will provide you results showing various SCADA software products. Many will claim you can download them for free. But not all these products truly offer free SCADA software. Supervisory Control and Data Acquisition (SCADA) software is a powerful tool. With the power of SCADA, your business can monitor, control, visually track […]
Malicious attacks by hackers and state-sponsored actors to disrupt industrial control systems using SCADA is a growing concern. Recent breaches of SCADA network security in Ukraine, the United States and other nations have underscored the seriousness of the threat. As a result, the U.S. government has issued an advisory warning that hackers have made attempts […]
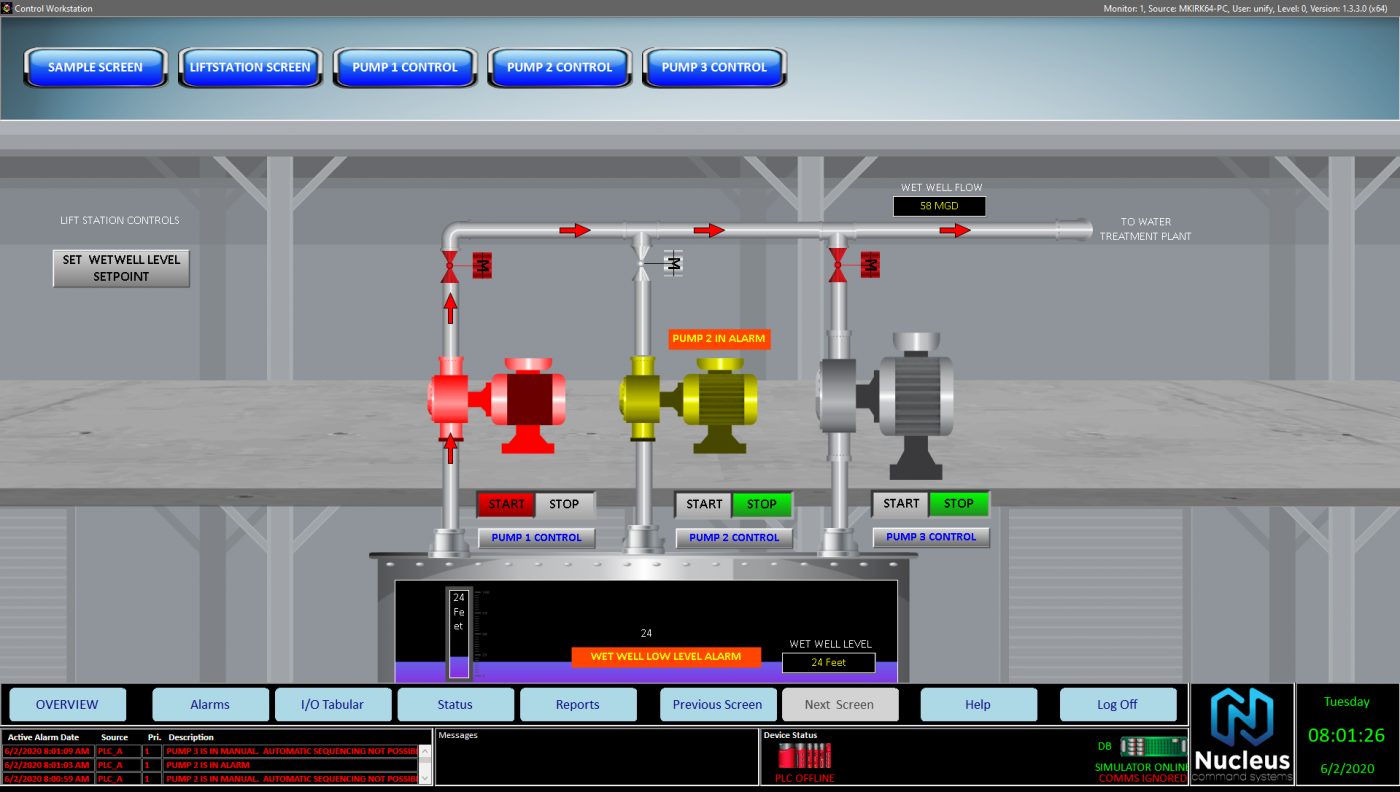
Water and wastewater system operators have critical requirements for their SCADA systems Water and wastewater treatment plants perform a vital role. Communities and businesses require clean, safe and efficient treatment of water. And a major key to achieving this goal is installing the right SCADA system for water and wastewater treatment. It’s essential that SCADA […]
Systems Integration expert Vance VanDoren endorses the Nucleus HMI SCADA software platform due to its reliability and affordability.
Nucleus Command Systems announces addition of new communication protocols to groundbreaking SCADA platform solution.
Public utility systems such as power, water and wastewater management have been one of the most successful applications for HMI SCADA technology. Government agencies learned about the productivity, safety and efficiency gains decades ago. Public rail transit systems worldwide began utilizing control system software tools (such as Nucleus) to safely and efficiently move millions of […]
SCADA systems stand to benefit greatly from the technology of the Internet of Things. The IoT could enable a revolution in SCADA design.
An interview with Nucleus executive Kevin Jiang about the HMI SCADA system features.
- 1
- 2